We’ve all been guilty of it. You find an orphan USB drive. If it’s less than 8GB nowadays, you probably bin it. After all, the chances of locating the owner are about exactly zero. But 8GB or better is an invitation to additional storage. So we keep it for ‘a spare’.
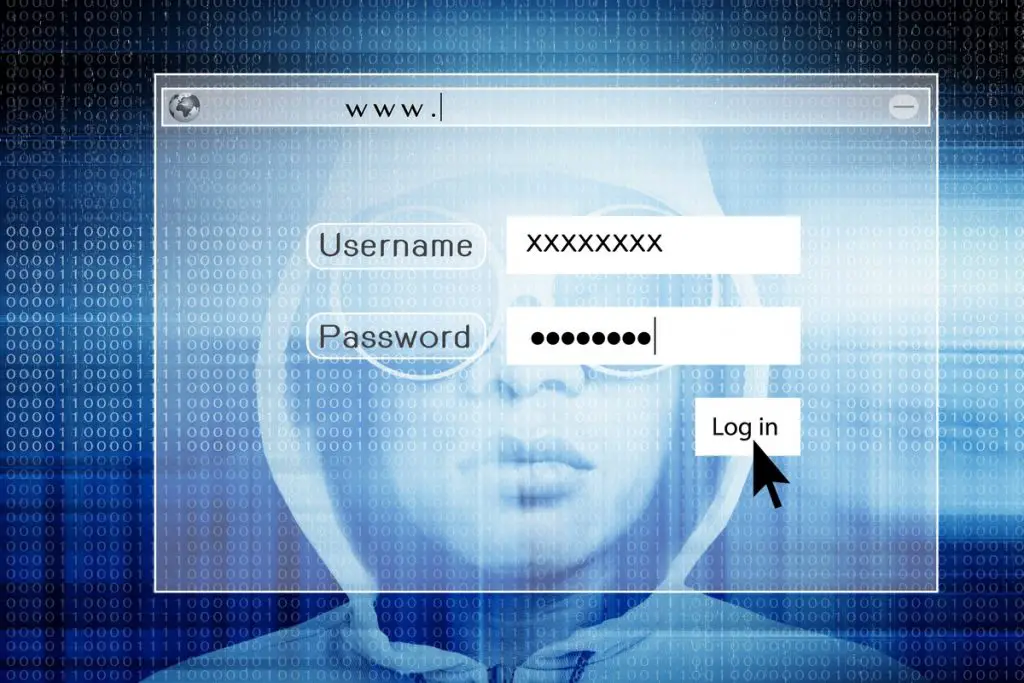
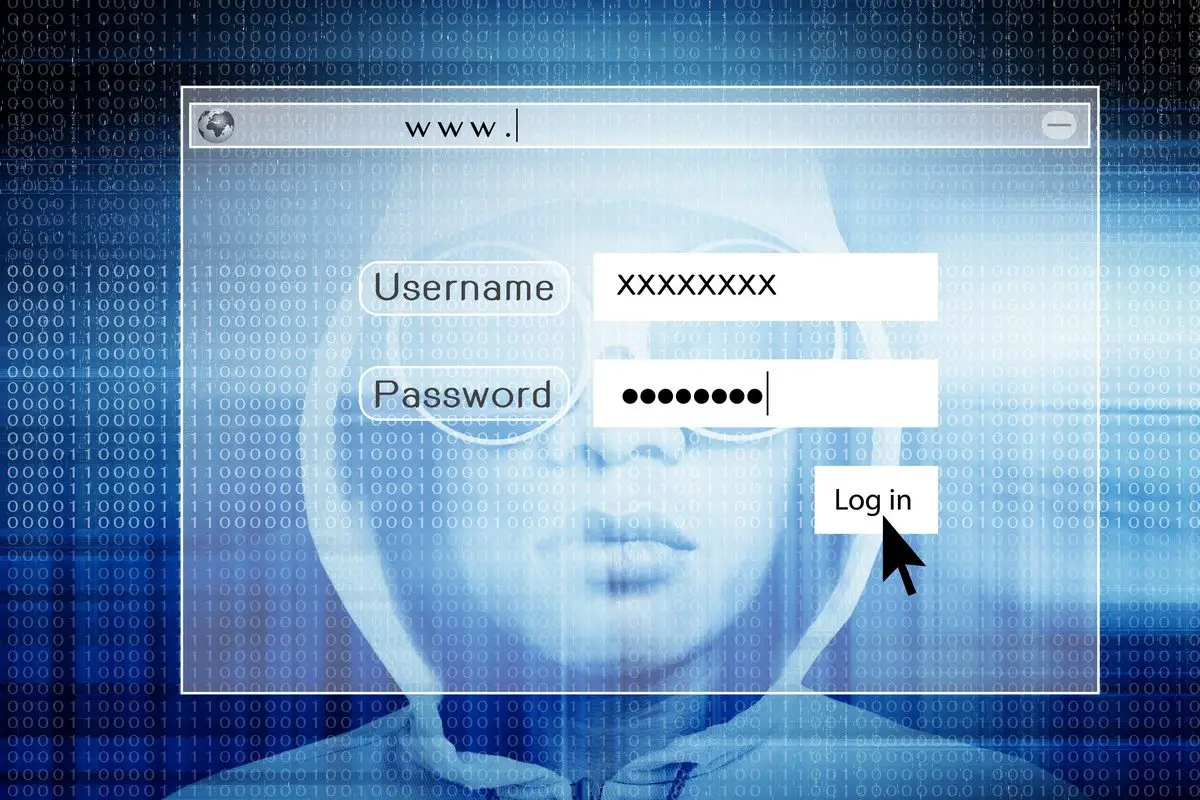
Sooner or later it surfaces. You insert it and, if you’re really smart, scan it. Then you delete the files that are on it and start using it. What you don’t know is that a hacker may now be getting all your passwords even if you’ve reformatted it!
USB drives and malware…
Most of us are aware of the risks associated with malware. Yet, according to American research, 75% of us are likely to use a USB drive we have found. Even after formatting, hidden partitions can still be activated.
In a report released today, researchers at the University of Adelaide have shaken the security conscious. They announced that removable USB sticks that have been tampered with, can detect signals from other USB ports on that device. For example, that thumb drive can be logging and transmitting keystrokes from your keyboard. Or it could be scanning data on a second USB drive. It’s a tactic known as information “leakage”.
According to one of the authors of the report, Dr Yuval Yarom, hackers can use that drive to ‘listen’ for passwords and other sensitive information.
“When you connect several devices to USB ports, one device can listen to the information that other devices send to the computer. A malicious USB is able to listen to communication, to what your keyboard sends to the computer, and can acquire passwords.”
Everything in a computer is interconnected. USB ports are connected to the motherboard and through that to your Wi-Fi and Bluetooth circuits. By installing code that activates on certain triggers, hackers could then access your data via Bluetooth or even SMS.
The information ‘leakage’ risk was initially detected by Adelaide computer science student Yang Su. Together with other research academics, he then tested 50 different computers for USB ‘leakage’. The bad news is that fully 90% of those computers leaked data.
The research results are to be presented at a conference for computer security professionals in Vancouver next week.
Given the very low cost of USB drives and TF cards today (less than $0.50 per gigabyte), I suggest you leave that USB drive exactly where you found it. What do you say?